 Man, Glenn Greenwald at the UK Guardian has got a very good, and very high-level, source (or sources).
Man, Glenn Greenwald at the UK Guardian has got a very good, and very high-level, source (or sources).
After his Wednesday blockbuster release of secret court documents detailing an order to release millions of Verizon phone records to the NSA, and his arguably more disturbing Thursday blockbuster release of classified documents detailing the secret PRISM program allowing the government "direct access" to the servers of giant Internet service providers like Microsoft, Yahoo!, YouTube, Google and Skype, he has, as promised earlier today, just released another major classified document.
This one is a classified 18-page Presidential Policy Directive issued by President Obama last October detailing "Offensive Cyber Effects Operations (OCEO)" which "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging".
It is said, by an Administration national security spokesperson, to be an update to "a similar directive dating back to 2004."
Here are the key details from Greenwald's latest blockbuster report, written along with the Guardian's Ewen MacAskill...
The 18-page Presidential Policy Directive 20, issued in October last year but never published, states that what it calls Offensive Cyber Effects Operations (OCEO) "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging".
It says the government will "identify potential targets of national importance where OCEO can offer a favorable balance of effectiveness and risk as compared with other instruments of national power".
The directive also contemplates the possible use of cyber actions inside the US, though it specifies that no such domestic operations can be conducted without the prior order of the president, except in cases of emergency.
The aim of the document was "to put in place tools and a framework to enable government to make decisions" on cyber actions, a senior administration official told the Guardian.
...
The directive's publication comes as the president plans to confront his Chinese counterpart Xi Jinping at a summit in California on Friday over alleged Chinese attacks on western targets.
Even before the publication of the directive, Beijing had hit back against US criticism, with a senior official claiming to have "mountains of data" on American cyber-attacks he claimed were every bit as serious as those China was accused of having carried out against the US.
...
The document says that agencies should consider the consequences of any cyber-action. They include the impact on intelligence-gathering; the risk of retaliation; the impact on the stability and security of the internet itself; the balance of political risks versus gains; and the establishment of unwelcome norms of international behaviour.
...
The revelation that the US is preparing a specific target list for offensive cyber-action is likely to reignite previously raised concerns of security researchers and academics, several of whom have warned that large-scale cyber operations could easily escalate into full-scale military conflict.
...
The full classified directive repeatedly emphasizes that all cyber-operations must be conducted in accordance with US law and only as a complement to diplomatic and military options. But it also makes clear how both offensive and defensive cyber operations are central to US strategy.
...
The directive provides that any cyber-operations "intended or likely to produce cyber effects within the United States" require the approval of the president, except in the case of an "emergency cyber action". When such an emergency arises, several departments, including the department of defense, are authorized to conduct such domestic operations without presidential approval.
...
Earlier this year, the Pentagon publicly accused China for the first time of being behind attacks on the US. The Washington Post reported last month that Chinese hackers had gained access to the Pentagon's most advanced military programs.
The director of national intelligence, James Clapper, identified cyber threats in general as the top national security threat.
Obama officials have repeatedly cited the threat of cyber-attacks to advocate new legislation that would vest the US government with greater powers to monitor and control the internet as a means of guarding against such threats.
...
In a statement, Caitlin Hayden, national security council spokeswoman, said: "We have not seen the document the Guardian has obtained, as they did not share it with us. However, as we have already publicly acknowledged, last year the president signed a classified presidential directive relating to cyber operations, updating a similar directive dating back to 2004. ... The procedures outlined in this directive are consistent with the US Constitution, including the president's role as commander in chief, and other applicable law and policies."
• Today's full Greenwald/MacAskill report is posted here.
• The complete October 2012 Presidential Directive on "Offensive Cyber Effects Operations" is posted here.


 'Green News Report' 5/6/25
'Green News Report' 5/6/25
 Prosecutors Resign After Trump U.S. Attny Strikes Deal With Felon Cop: 'BradCast' 5/5/25
Prosecutors Resign After Trump U.S. Attny Strikes Deal With Felon Cop: 'BradCast' 5/5/25 Sunday 'Good Buy, Dolly!' Toons
Sunday 'Good Buy, Dolly!' Toons Trump Losing Streak Continues into SECOND Hundred Days: 'BradCast' 5/1/25
Trump Losing Streak Continues into SECOND Hundred Days: 'BradCast' 5/1/25 'Green News Report' 5/1/25
'Green News Report' 5/1/25 100 Daze: 'BradCast' 4/30/25
100 Daze: 'BradCast' 4/30/25 Campaign to 'Impeach Trump Again' Gains Fresh Momentum: 'BradCast' 4/29/25
Campaign to 'Impeach Trump Again' Gains Fresh Momentum: 'BradCast' 4/29/25 'Green News Report' 4/29/25
'Green News Report' 4/29/25 And Then They Came for the Judges...: 'BradCast' 4/28/25
And Then They Came for the Judges...: 'BradCast' 4/28/25 Sunday 'Desperation' Toons
Sunday 'Desperation' Toons Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25
Trump EPA Guts Enviro Justice Office: 'BradCast' 4/24/25 'Green News Report' 4/24/25
'Green News Report' 4/24/25 Sunday
Sunday  Largest U.S. Broad-caster Hoaxes Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25
Largest U.S. Broad-caster Hoaxes Viewers to Help Gut FCC Rules: 'BradCast' 4/23/25 FCC on Precipice of Ending All Limits on Corp. Control of Local TV Stations
FCC on Precipice of Ending All Limits on Corp. Control of Local TV Stations GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25
GOP Earth Day 2025 Hypocrisies and Dilemmas: 'BradCast' 4/22/25 Pope Francis Dies, Trump Still Alive and Criming: 'BradCast' 4/21/25
Pope Francis Dies, Trump Still Alive and Criming: 'BradCast' 4/21/25 Soc. Sec. Expert Warns DOGE of Collapse, Privatization: 'BradCast' 4/10/2025
Soc. Sec. Expert Warns DOGE of Collapse, Privatization: 'BradCast' 4/10/2025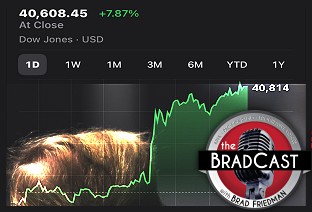 Trump Blinks, Chaos Reigns, Markets Spike Amid Tariff 'Pause': 'BradCast' 4/9/25
Trump Blinks, Chaos Reigns, Markets Spike Amid Tariff 'Pause': 'BradCast' 4/9/25 SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25
SCOTUS Deportation Ruling Grimmer Than First Appears: 'BradCast' 4/8/25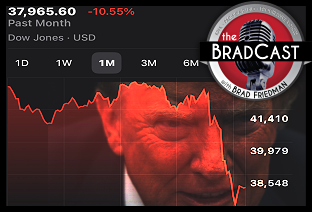 Cliff Diving with Donald: 'BradCast' 4/7/25
Cliff Diving with Donald: 'BradCast' 4/7/25
 VA GOP VOTER REG FRAUDSTER OFF HOOK
VA GOP VOTER REG FRAUDSTER OFF HOOK Criminal GOP Voter Registration Fraud Probe Expanding in VA
Criminal GOP Voter Registration Fraud Probe Expanding in VA DOJ PROBE SOUGHT AFTER VA ARREST
DOJ PROBE SOUGHT AFTER VA ARREST Arrest in VA: GOP Voter Reg Scandal Widens
Arrest in VA: GOP Voter Reg Scandal Widens ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC
ALL TOGETHER: ROVE, SPROUL, KOCHS, RNC LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States'
LATimes: RNC's 'Fired' Sproul Working for Repubs in 'as Many as 30 States' 'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States
'Fired' Sproul Group 'Cloned', Still Working for Republicans in At Least 10 States FINALLY: FOX ON GOP REG FRAUD SCANDAL
FINALLY: FOX ON GOP REG FRAUD SCANDAL COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION
COLORADO FOLLOWS FLORIDA WITH GOP CRIMINAL INVESTIGATION CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL
CRIMINAL PROBE LAUNCHED INTO GOP VOTER REGISTRATION FRAUD SCANDAL IN FL Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV
Brad Breaks PA Photo ID & GOP Registration Fraud Scandal News on Hartmann TV  CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM
CAUGHT ON TAPE: COORDINATED NATIONWIDE GOP VOTER REG SCAM CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM
CRIMINAL ELECTION FRAUD COMPLAINT FILED AGAINST GOP 'FRAUD' FIRM RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL
RICK SCOTT GETS ROLLED IN GOP REGISTRATION FRAUD SCANDAL VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV
VIDEO: Brad Breaks GOP Reg Fraud Scandal on Hartmann TV RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD
RNC FIRES NATIONAL VOTER REGISTRATION FIRM FOR FRAUD EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud
EXCLUSIVE: Intvw w/ FL Official Who First Discovered GOP Reg Fraud GOP REGISTRATION FRAUD FOUND IN FL
GOP REGISTRATION FRAUD FOUND IN FL

































